A Biased View of Aws Backup
Table of ContentsWhat Does Aws Cloud Backup Do?The Main Principles Of Aws Cloud Backup The Facts About Aws Backup UncoveredEc2 Backup Fundamentals ExplainedData Protection Things To Know Before You Get ThisSome Known Details About Rto
The GDPR emphasizes the individual information legal rights of EU homeowners, consisting of the right to alter, access, erase, or transfer their information. Individual data refers to any type of information that connects to a person.
To keep their information offered at all times, firms require to keep the IT framework energetic even when it comes to a calamity. This state of surefire access to information is called data availability. This article assesses the fundamentals of data availability and also its difficulties, and supplies methods to keep a high level of information accessibility.
Without a correct data safety policy, delicate info can fall into the hands of enemies, enabling them to get access to your network, and also expose the personal info of consumers as well as staff members. This write-up presents the concept of data protection and the different devices and techniques you can make use of to safeguard your information and avoid a calamity.
Rumored Buzz on Aws Backup
File encryption makes sure the integrity of information by shielding it from unapproved modification. Security minimizes the danger of accessing data from untrustworthy sources by verifying information's source.
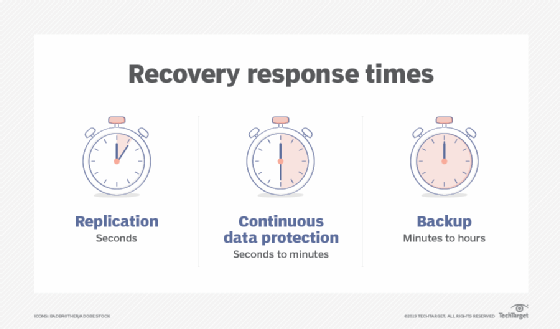
A constant information security system keeps a record of all information changes as well as allows you to restore a system to any kind of previous point. This kind of backup fixes the issue of shedding data developed in between two set up back-ups. It likewise provides protection versus strikes like ransomware or malware, as well as unintended removal of data.
Any type of firm that processes and stores individual data of EU residents, also if it is not literally located in the EU, need to use to the GDPR rules. There are two major duties in the GDPR: the GDPR Information Processor is an entity that holds or refines this kind of information on behalf of an additional organization, as well as a GDPR Information Controller that collects or processes personal data for its very own objectives.
Immutable S3 objects are safeguarded using object, or bucket-level arrangement of WORM and retention qualities. This functionality gives both information security, including extra defense versus unexpected or harmful removal as well as ransomware as well as regulative conformity.
The 10-Minute Rule for Protection Against Ransomware

Information security is the procedure of guarding important details from corruption, compromise or loss. The significance of data defense boosts as the amount of information developed and kept remains to expand at unprecedented rates. There is likewise little resistance for downtime that can make it difficult to access essential details.

The essential principles of data protection are to protect and make available data under all circumstances.
The Ultimate Guide To Rto
Information lifecycle administration is a thorough technique for valuing, cataloging as well as shielding information possessions from application and also customer mistakes, malware and virus assaults, maker failing or center blackouts as well as disruptions. Much more just recently, information monitoring has actually come to consist of locating means to open business worth from or else dormant duplicates of information for coverage, test/dev enablement, analytics and also various other objectives.
Storage space technologies for safeguarding data include a disk or tape back-up that copies designated info to a disk-based storage range or a tape cartridge. Tape-based backup is a strong option for data protection versus cyber strikes. Accessibility to tapes can be sluggish, they are portable and inherently offline when not loaded in a drive, and also hence risk-free from dangers over a network. https://www.kickstarter.com/profile/1938076379/about.
Storage space pictures can immediately generate a collection of guidelines to info saved on tape or disk, making it possible for faster information healing, while continuous information security (CDP) supports all the data in an enterprise whenever a change is made. Information portability-- the capacity to move information amongst different application programs, calculating atmospheres or cloud services-- provides another collection of issues and remedies for data defense.
Some Of Data Protection
Information defense is the procedure of guarding important information from corruption, concession or loss. The relevance of information defense increases as the quantity of information developed and also kept proceeds to grow at unmatched rates. There is also little resistance for downtime that can make it difficult to accessibility vital info (https://www.ultrabookmarks.com/author/clumi0/).
Protecting information from compromise and making certain data personal privacy are other key parts of information protection. The coronavirus pandemic created countless employees to function from home, causing the need for remote information protection. Companies have to adapt to guarantee they are safeguarding information wherever staff members are, from a central data facility in the office to laptop computers at home.
The crucial principles of data defense are to protect as well as offer data under all conditions. The term data defense describes both the operational back-up of information as well as service continuity/disaster recovery (BCDR). Data security approaches are developing along 2 lines: data accessibility and information management. Data accessibility makes certain users have the data they require to perform business even if the data is damaged or shed.
Details lifecycle monitoring is a thorough method for valuing, cataloging as well as safeguarding information properties from application as well as user mistakes, malware and also infection attacks, maker failure or center blackouts and disruptions. A lot more lately, information management has actually come to include locating methods to open service value from or else inactive copies of information for reporting, test/dev enablement, analytics and also other purposes.
More About S3 Cloud Backup
Storage modern technologies for protecting data include a disk or tape backup that duplicates designated information to a disk-based storage array or a tape cartridge. Tape-based backup is a strong option for data protection against cyber strikes. Although access to tapes can be slow, they are mobile as well as inherently offline when not packed in a drive, and also thus safe from risks over a network.
Storage snapshots can automatically generate a collection of reminders to info kept on tape or disk, making it possible for faster data recovery, while continuous data protection (CDP) supports all the information in a business whenever a change is made. Information mobility-- the ability to relocate data among various application programs, calculating atmospheres or cloud services-- offers an additional collection of issues as well as services for data protection.